As we enter 2026, the cybersecurity landscape is entering its most transformative period in decades. For organizations large and small, the coming year will be defined not by entirely new categories of threats, but by the unprecedented scale, intelligence, and automation behind existing ones. Cybersecurity is no longer merely an IT discipline; it has become “mission assurance” and a core determinant of operational stability.
AI Becomes the Attacker’s Operating System
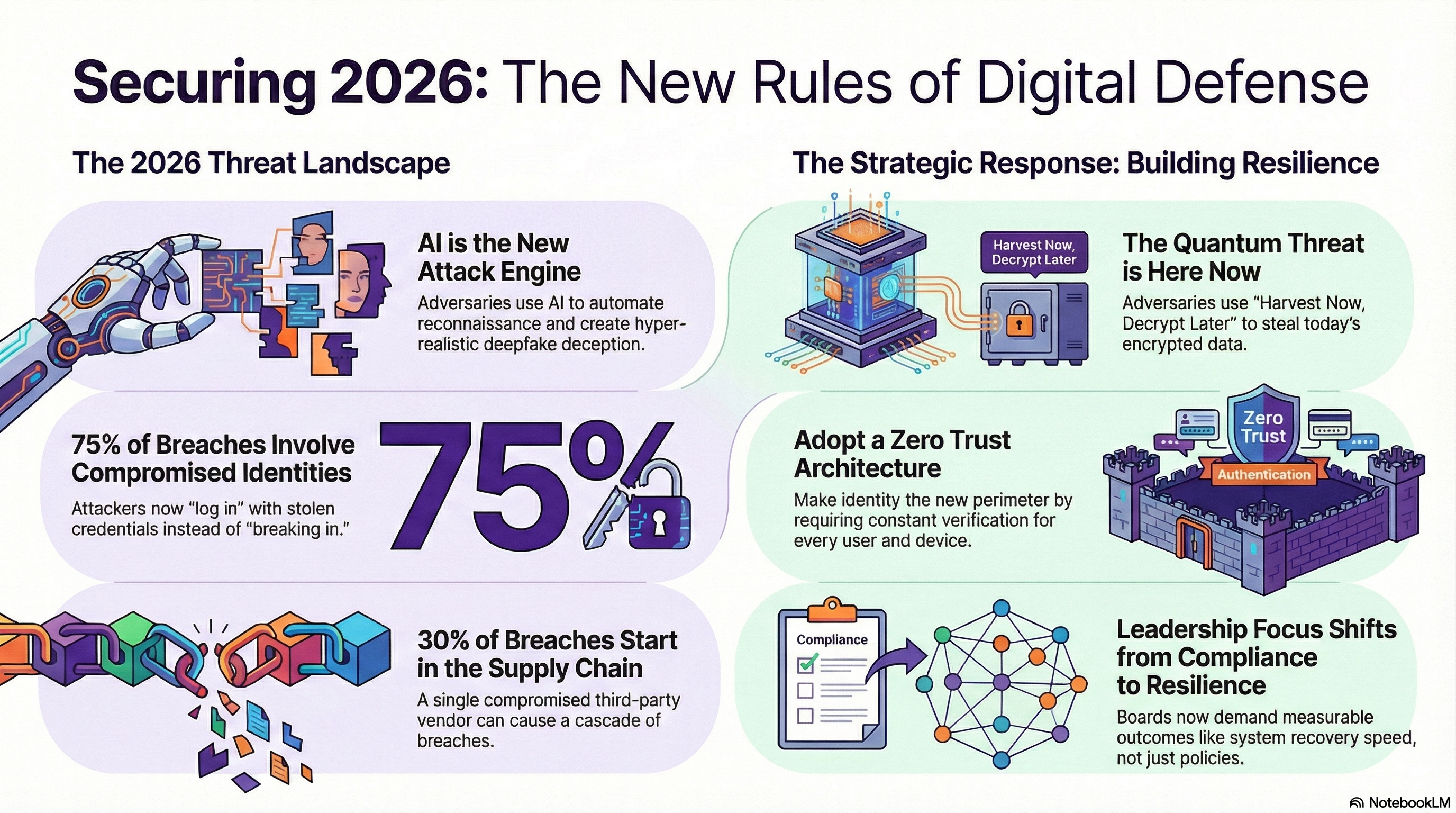
In 2026, Artificial Intelligence will move from a helpful tool to the engine running the modern cyberattack. Adversaries are increasingly using AI to automate reconnaissance, develop complex exploit chains, and craft hyper-personalized phishing at an industrial scale.
- The Renaissance of Social Engineering: AI-driven deepfakes—incorporating near-perfect voice and video impersonation—will make social engineering nearly indistinguishable from legitimate communication. This “New Age of Deception” means authenticity will become a top risk for brands and executives alike.
- Agentic AI as a New Attack Surface: Autonomous AI agents, designed to act on behalf of users and systems, will handle complex tasks like triaging and writing API calls. However, these agents often have broader system-level permissions than employees, making them a potent new “insider threat” if compromised.
- AI vs. AI Warfare: Cybersecurity is evolving into a contest of machine intelligence. Only AI-supported defense can match AI-powered offense, leading to a global cyber arms race where both sides evolve in near real-time.
Identity: The Real Perimeter
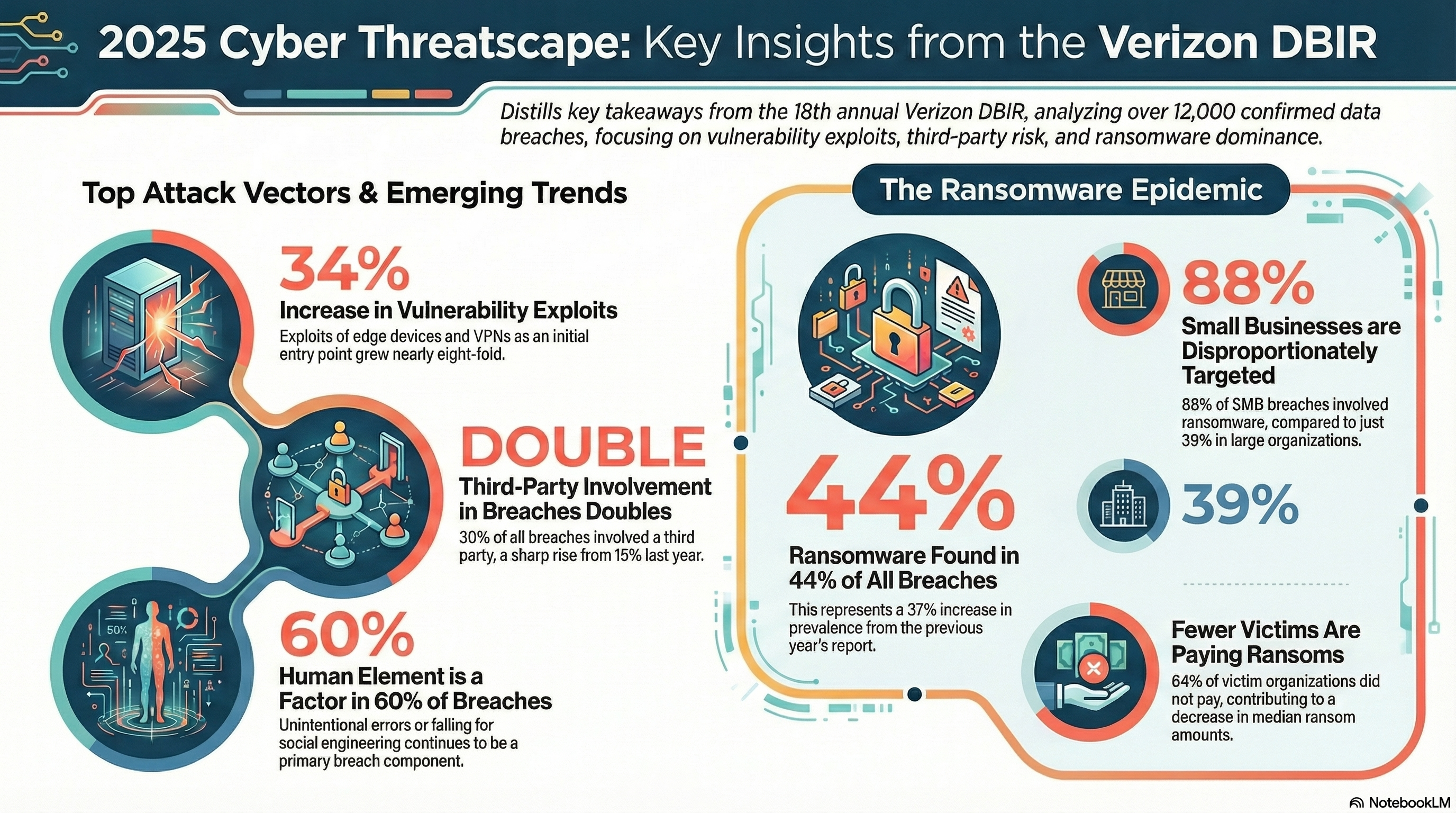
The traditional boundary-based security model is officially obsolete; Identity compromise remains the dominant cause of breaches, with 75% of intrusions involving compromised identities or valid credentials rather than malware.
- Logging In vs. Breaking In: Adversaries are increasingly choosing to “log in” using stolen or guessed credentials rather than “breaking in” through technical exploits. This shift makes Identity and Access Management (IAM) the central battlefield of 2026.
- The Explosion of Non-Human Identities: Experts predict that “agentic identities”—belonging to AI bots and automated systems—will outnumber human ones by as much as 80 or 100 to 1. Managing this “identity sprawl” is critical, as machine identities often accumulate opaque, over-permissive access that is rarely reviewed.
- The Path to Zero Trust: Modernizing IAM strategies with Zero Trust principles—requiring constant verification for every user and device—is the fastest path to measurable risk reduction.
The Supply Chain Reality Check
Third-party involvement in breaches has doubled recently, now appearing in 30% of all confirmed data breaches. Adversaries have learned that one weak supplier can compromise dozens of organizations simultaneously, targeting managed service providers, cloud platforms, and niche subcontractors.
- The “Boomerang Effect”: In critical infrastructure, supply chains are so deeply intertwined that a disruption in one sector—like a fuel pipeline—can cascade into transportation, food supply, and government services. In some cases, a digital service imported from one country can be consumed by another, only for the impact of a breach to “boomerang” back to the original exporter.
- Contractual Resilience: Traditional vendor questionnaires are becoming obsolete. 2026 will demand continuous visibility into supplier controls and the inclusion of clear penalty, termination, and cybersecurity clauses in vendor contracts.
The Quantum Imperative: “Harvest Now, Decrypt Later”
While a functional, large-scale quantum computer may still be years away, quantum risk is a present-tense operational threat.
- Mosca’s Theorem: Organizations must act now because of “Harvest Now, Decrypt Later” (HNDL) strategies, where adversaries intercept and store encrypted sensitive data today with the intent of cracking it once quantum capabilities mature. If the time your data needs to remain secret plus the time it takes to migrate your systems exceeds the time until a quantum break, your data is already at risk.
- Post-Quantum Cryptography (PQC): The US National Institute of Standards and Technology (NIST) has finalized the first standards for PQC (e.g., ML-KEM and ML-DSA). Leading organizations are already piloting hybrid cryptography, combining classical and quantum-resistant algorithms to ensure defense-in-depth during the transition.
Resilience as a Board-Level Metric
By 2026, cybersecurity will be judged on measurable outcomes rather than the mere presence of tools or policies. Boards are shifting their focus from simple compliance status to “resilience readiness,” prioritizing metrics such as system recovery speed, network segmentation effectiveness, and backup immutability.
The gap between organizations that act now to operationalize resilience and those that treat security as a paperwork exercise will widen beyond what traditional programs can close. For the modern enterprise, cybersecurity is no longer an option—it is the backbone of national and corporate readiness.
Analogy for Understanding: Think of your 2026 security posture not as a static fortress wall, but as a high-tech airport security system. It’s not enough to just check a ticket at the front gate (the perimeter). You must constantly verify identities at every terminal, elevator, and boarding gate (Zero Trust/IAM). Just as an airport relies on an intricate web of fuel suppliers, baggage handlers, and air traffic control (the Supply Chain), one failure anywhere can ground the entire operation. Finally, you must prepare for the “Quantum Storm” on the horizon; even if it hasn’t hit yet, the planes you’re building today must be engineered to withstand it, or they’ll be grounded the moment it arrives.