The Quantum Countdown: Preparing Your Organization for a Post-Quantum World
Quantum computing is no longer a distant theoretical concept; it is on the horizon, bringing a seismic shift in how organizations must approach cybersecurity risk. The advent of future quantum machines introduces the threat of quantum decryption, which could fundamentally undermine the trust, confidentiality, and resilience of digital business.
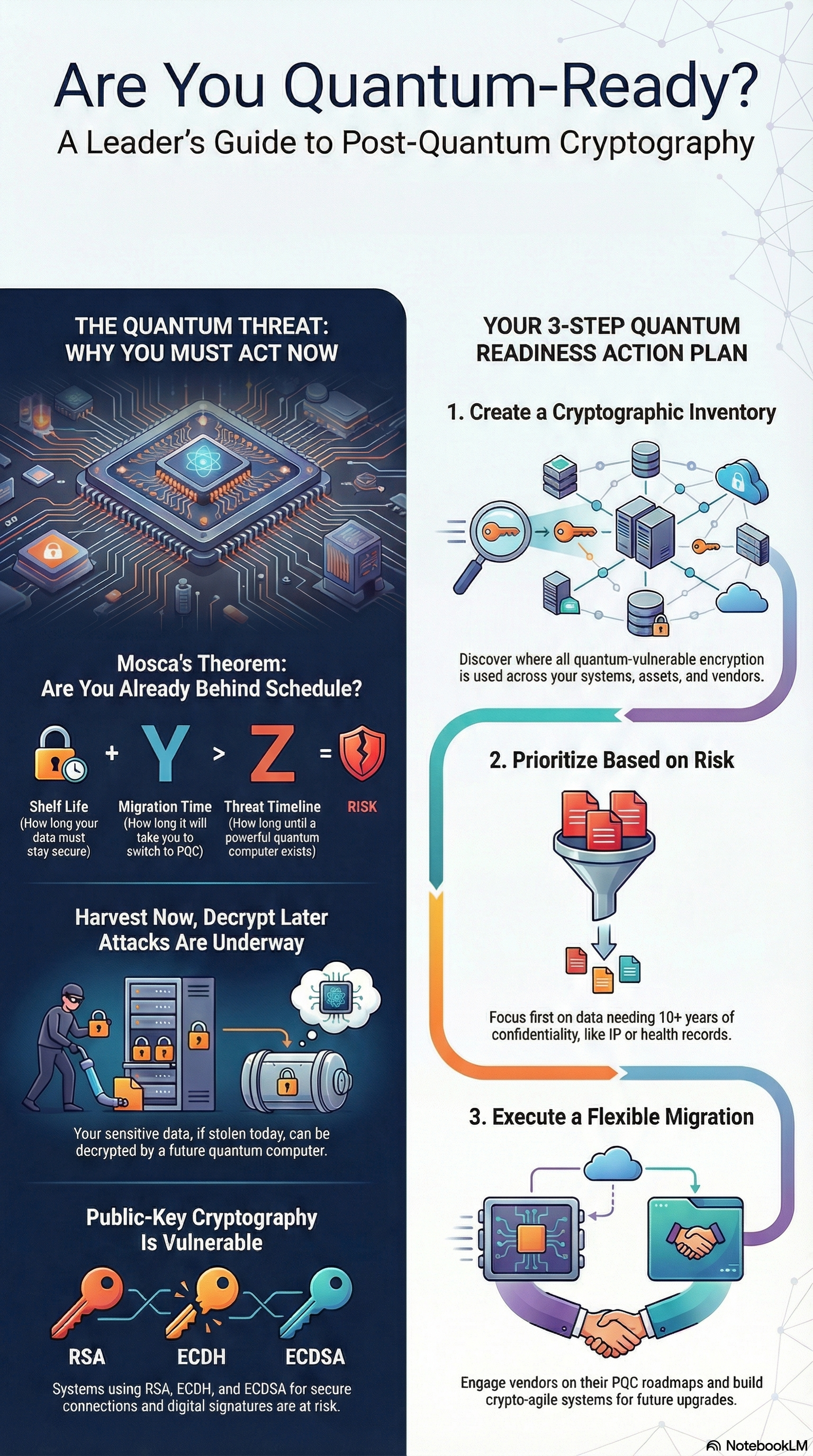
While the technology offers transformative potential for fields like drug discovery and financial modeling, it also poses a “harvest now, decrypt later” (or Store Now, Decrypt Later - SNDL) threat. This means adversaries may be capturing encrypted sensitive data today with the intent to break its protections once powerful quantum computers become available.
The Math of Urgency: Mosca’s Theorem
To understand how quickly your organization needs to act, we can look to Mosca’s Theorem. This risk assessment framework suggests that organizations need to worry if X + Y > Z, where:
- X = The amount of time data needs to remain secure (shelf life).
- Y = The time it takes to migrate your organization to post-quantum cryptographic (PQC) solutions.
- Z = The time before a sufficiently strong quantum computer exists to break current encryption.
With many experts predicting the “threat timeline” (Z) could be as early as 2030 or 2035, and considering that major security upgrades often take years, many organizations may already be behind schedule.
A Strategic Roadmap for Readiness
Transitioning to quantum-safe security is not a quick fix; it is a multi-year organizational transformation. Based on guidance from the sources, here is how to build your roadmap.
1. Establish Leadership and Governance
Quantum risk is a strategic business risk, not just an IT issue. It requires:
- Executive Buy-in: Board-level discussions should frame quantum readiness as a matter of business continuity and customer trust.
- Clear Ownership: Designate a senior leader, such as a CISO or CTO, with the authority to coordinate across legal, procurement, and business units.
- Compliance Alignment: Ensure policies reflect emerging standards from agencies like NIST and CISA.
2. Conduct a Cryptographic Inventory
You cannot protect what you do not know you have. Organizations should use automated scanning tools or resources like the PQC Inventory Workbook to map their cryptographic assets. This inventory must include:
- Network Security: HTTPS connections, VPNs, and secure file transfers.
- Authentication: Digital certificates and multi-factor authentication systems.
- Data at Rest: Encrypted databases, backups, and cloud storage.
3. Prioritize Based on Risk
Not every system needs to be upgraded simultaneously. Focus first on high-priority assets:
- Data requiring confidentiality for 10+ years (e.g., intellectual property, health records).
- Critical infrastructure and operational technology.
- Long-term contracts and legal archives.
4. Build for “Cryptographic Agility”
One of the most vital strategies is cryptographic agility—the ability to rapidly swap security methods without rebuilding entire systems from scratch.
Think of it like building a house with replaceable appliances rather than hardwiring everything into the walls. When technology improves, you can upgrade individual components without tearing down the whole structure.
The Human Element: Building Quantum-Ready Teams
The transition requires more than just new math; it requires a skilled workforce. The industry currently faces a significant talent shortage, particularly for “bridge professionals” who can translate between technical quantum capabilities and business value. HR departments should implement tiered training programs, ranging from basic quantum awareness for all staff to hands-on proficiency for technical teams.
Immediate Action Plan
If you are just starting, focus on these milestones:
- In the next 30 days: Brief executive leadership on the 5-10 year threat timeline and assign an internal owner for quantum readiness.
- In the next 90 days: Complete a comprehensive cryptographic inventory and assess the quantum readiness of your critical vendors.
- Ongoing: Monitor developments from quantum leaders (like IBM and Google) and stay updated on the evolving NIST post-quantum standards.
Next Steps
Listen to the Quantum Decryption Action Plan podcast episode for a deeper dive into the topic.
Conclusion
The quantum threat is unique because we have advance warning. Unlike sudden zero-day exploits, we can see quantum decryption coming. Starting your journey today is not just about avoiding risk; it is about maintaining a competitive advantage and demonstrating that your organization takes long-term security seriously.